Challenges to LEO HTS Megaconstellations
by Muhammad Furqan and Zoe Shahid
Brisbane, Australia, September 4, 2020--Exponentially increasing numbers of announced ambitious NGSO (Non-Geo Stationary Orbit) or LEO-HTS (Lower Earth Orbit – High Throughput Satellites) Mega Constellations have been creating waves in the world of technology. Their success will not be a mere disruption to the existing system, it will be a whole new system altogether.
With regular revisions in numbers of satellites from existing players and entrance of new players, these mega constellations will redefine the dynamics of Space Race 2.0, Industry 4.0, 4th, and 5th Dimension Warfare. With the rollout of a complete extra-terrestrial network there will be multiple challenges faced by the new ecosystem. With multiple revisions of filings with FCC (Federal Communication Commission) OneWeb (Qualcomm, Virgin, Airbus) leads the race with 48,000 satellites followed StarLink of SpaceX with 42,000 and Project Kuiper of Amazon with 3300 (1st numbers, may revise with the trend of the competitors) odd and other multiple constellations of smaller numbers. Recently, Huawei also announced its arrival with China Unicom with numbers of satellites not yet publicly announced.
Security Challenges
One of the biggest challenges faced by these mega constellations is ‘Cyber Security’. Satellite Communications has been serving the world for different services for more than half a century. In this article, we will focus on the security challenges faced by the LEO constellations and will deal with other challenges in subsequent articles.
Traditional GEO Satellite Communication Networks have remained secure so far due to limited integration with the ground networks. These networks rely on not easily available specialized communication equipment, specific frequencies, and some additional technical skills to establish a successful connection. The sophistication of the equipment, technical parameters, skills altogether with costs involved have made commissioning of even a legal link a perplexing task, making it even more difficult for illegal connections or eavesdropping.
Moreover, traditional satellite communications links were only receive-amplify-transmit kind of connections working only on the physical layer of the OSI, TCP/IP, UDP architectures. Except for MSS services, Customer networks are not usually directly connected to the satellite but through specialised interfaces of satellite communication equipment. Customers network interface with the public ground networks, PSTN/Cloud/Cellular/Fibre, are more vulnerable to intrusion as compared to their satellite communication interface. This uniqueness along with global coverage made satellite communication primary choice of strategic organizations.
However, the arrival of the first generation of NGSO mega constellations will change the outlook of the satellite communication horizons. With focus on provision of low latency, high throughput, global footprint broadband services, end user will be directly connected to the satellites. With easy to deploy and use terminals customers and their personal network of devices (IoT – Internet of Things) will be able to enjoy the luxury at par with at least 4G LTE (4th Generation of Mobile Communication – Long Term Evolution), and will serve their purpose to complement the future terrestrial networks like 5G (5th Generation of Mobile Communication). With the ever-increasing demand of the data traffic with requirements of lower latency for services to perform at their optimum scale, organizations currently using traditional GEO satellite communication services will also review their connectivity priorities.
Potential Threats
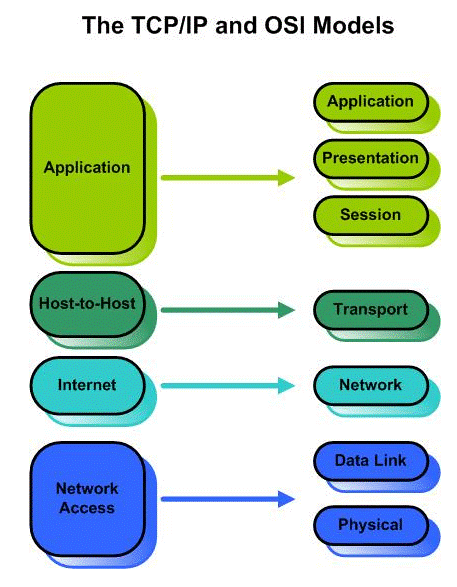 Change in the dynamics of the communication technologies will result in increase of potential possibilities of network, cyber a data security related risk. With end user direct connectivity with the satellites with lower cost easy to use and deploy terminals, no requirement of additional technical skillset, and satellites having on board processing to accommodate software-based networking technologies like SDN, SDR, NFV etc. can result in security breaches for the end-users, organizations, the network and even the satellites. It can be apprehended that the whole ecosystem of these mega constellations; customers, network, data traffic, communication interfaces, satellites, as all the layers of the OSI, TCP/IP or UDP models will be exposed, can at least expect similar threat level of any given terrestrial communication network. We can do the comparative and predictive analysis of the terrestrial network related security issues to map on the upcoming networks of the mega constellations.
Change in the dynamics of the communication technologies will result in increase of potential possibilities of network, cyber a data security related risk. With end user direct connectivity with the satellites with lower cost easy to use and deploy terminals, no requirement of additional technical skillset, and satellites having on board processing to accommodate software-based networking technologies like SDN, SDR, NFV etc. can result in security breaches for the end-users, organizations, the network and even the satellites. It can be apprehended that the whole ecosystem of these mega constellations; customers, network, data traffic, communication interfaces, satellites, as all the layers of the OSI, TCP/IP or UDP models will be exposed, can at least expect similar threat level of any given terrestrial communication network. We can do the comparative and predictive analysis of the terrestrial network related security issues to map on the upcoming networks of the mega constellations.
In this era where internet is the focal backend technology being used by the latest technological deployments and upcoming solutions in the form of IoT where the modern devices are connected with each other and communicate through the pool of wireless communications, with the help of embedded sensors which makes them smart enough to collect and analyse data and transmit over the internet. This data, hence, needs to be protected and secured. However, the nature of wireless media being shared and easily prone to interceptions, makes it more exposed towards security threats. Let us have a look at the common security threats and the areas where the wireless communications are making its application a challenge to be implemented on most of the crucial industries. Key areas which can be under threat are:
- Critical Information which is shared over the network.
- Nodes attached to the network; that can be servers or clients which have private information stored on them.
- Most importantly the network itself.
The elimination of threats to the information transmitted over the network is the major challenge in terrestrial communications systems. A few types of threats which can cause major damage to the vital areas described above are discussed briefly below:
Interception- this is the major challenge in shared network communications these days. Here the attacker intrudes the ongoing transmission through wiretapping or sniffing. This can cause the attacker to get access to authorized information and even credentials for the accounts transmitting the information.
Replay Attack- A replay attack which is commonly known and playback attack where the transmission packets are replayed with a delay to 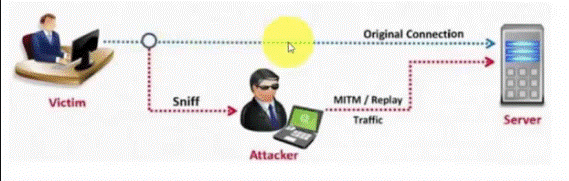 access certain information from the network. The picture below can be seen to understand the serious hazards of this issue.
access certain information from the network. The picture below can be seen to understand the serious hazards of this issue.
Spoofing- It is the action of camouflaging a message that can be in form of an email, text message, weblinks or a phone call, from a malicious sender and manipulated as being from a identified and reliable source. Spoofing can be done to an extent of masking the IP addresses to an allocated IP pool from the private network.
Manipulation of Data- This threat can cause to change the original information into something which is not the actual and authentic fact. Data alteration and access to the key resources is the most common risk when it comes to secure transmission and handling of critical information.
Most Authentication and Confidentiality protocols are implemented to mitigate the risk of security breaches in terrestrial communications but with the advancement in technology and shared network infrastructural approach in form of cloud networking, the risk and dangers are becoming more worse and a new challenge encountered by the industry.
Protocols
Another challenge in Communications Systems is that the security protocols for wireless and wired networks are different. Wireless communication and easily deployed but the security and bandwidth limitations are way more in number than in wired networks.
Now, these mega constellations and their users will be exposed to these threats and will require continuously evolving mitigation techniques to counter the threats. The security concerns do not end up here, but the physical security is another challenge. The 4th Dimension Warfare (Space Warfare) needs to be addressed as well, these satellites, although commercial entities, should be considered as critical strategic assets. In last few years we have experienced a growing trend of space warfare development, may it be the anti-satellite missiles testing by different countries or establishment of dedicated space force commands.
Conclusion
In conclusion the LEO HTS Mega Constellations are the centrepieces of the combined complex matrices of Industry 4.0, Space Race 2.0, 4th Dimension Warfare, and 5th Dimension Warfare (Cyber Warfare). These constellations will not only change the outlook of a night sky as we know it but will also play a considerable part in the change of life we are used to live.
------------------------------------------------
 With around a decade of experience in the satellite communications industry, Muhammad Furqan is a renowned writer and analyst with multiple publications and keynote appearances at different international platforms. Currently based in Australia, he is working in research related to Radio Frequency Electromagnetic Spectrum for mobile and satellite communications at Queensland University of Technology. He can be reached at: info@muhammadfurqan.com
With around a decade of experience in the satellite communications industry, Muhammad Furqan is a renowned writer and analyst with multiple publications and keynote appearances at different international platforms. Currently based in Australia, he is working in research related to Radio Frequency Electromagnetic Spectrum for mobile and satellite communications at Queensland University of Technology. He can be reached at: info@muhammadfurqan.com
 Zoe Shahid is an expert in Transmission Planning, Optimization and Operations with an experience of 12 years in maintaining and troubleshooting Fixed Line Fibre Optic Networks, providing seamless services. Currently based in Australia, she is gaining experience on network and cyber security along with providing her services for product and solution designs for Telecommunication Services providers. She can be reached at: zoe_shahid@hotmail.com
Zoe Shahid is an expert in Transmission Planning, Optimization and Operations with an experience of 12 years in maintaining and troubleshooting Fixed Line Fibre Optic Networks, providing seamless services. Currently based in Australia, she is gaining experience on network and cyber security along with providing her services for product and solution designs for Telecommunication Services providers. She can be reached at: zoe_shahid@hotmail.com